
Hunters is a SIEM Leader
Hunters recognized as a leader in Snowflake’s inaugural Cybersecurity Report.
Great SOCs Run on Hunters



Solve the challenges around data scale, cost and reliance on data engineers
Increase threat coverage while minimizing reliance on rule-writing

Significantly reduce time to containment and remediation
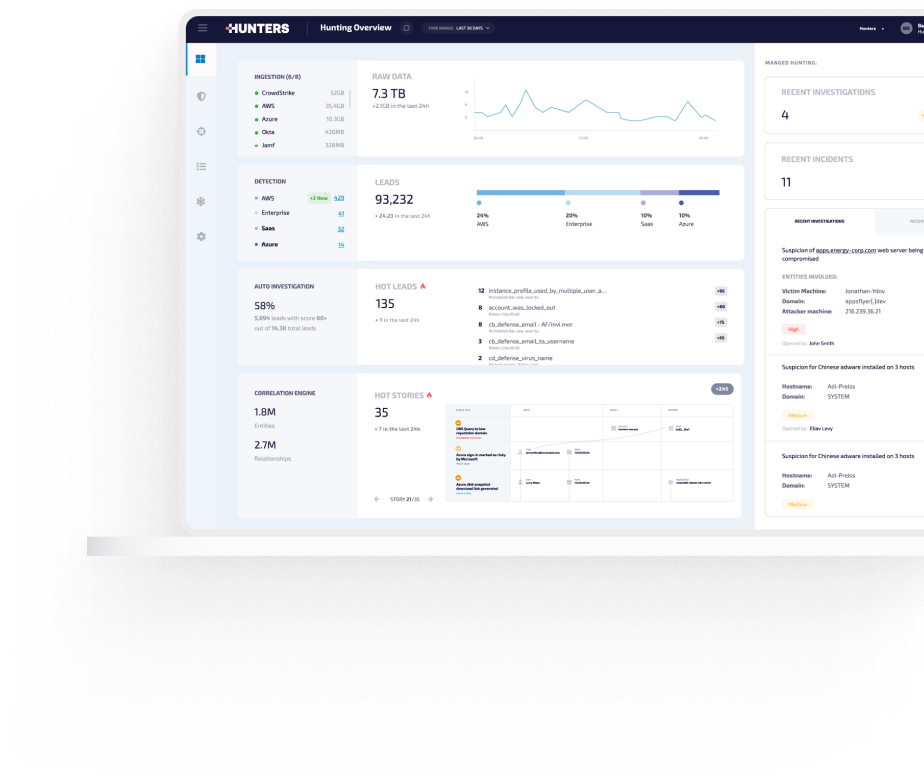
How it works
KEY CAPABILITIES
- DATA
- DETECTION
- Investigation
- Response
Ingest all your data
Break the paradigm of more data creating more noise, forcing increased staffing and budget.
Easily ingest and retain all your data, without compromise, at a predictable cost.
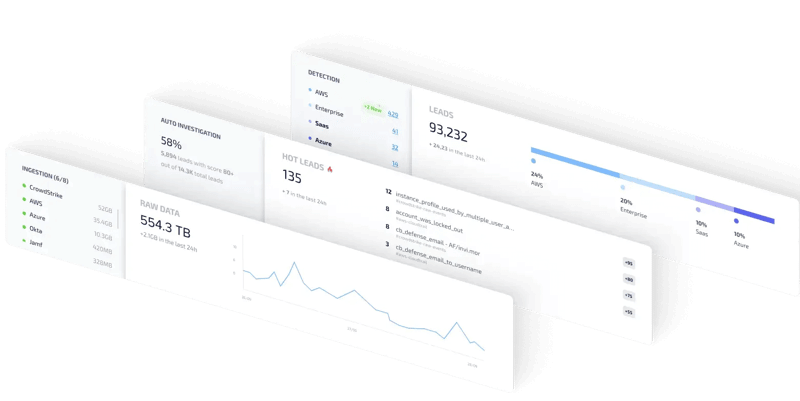
Detect incidents that matter
Hunters’ built-in, always up-to-date detectors eliminate the security engineering work for all common security use cases, removing the need to set up and maintain detection rules.
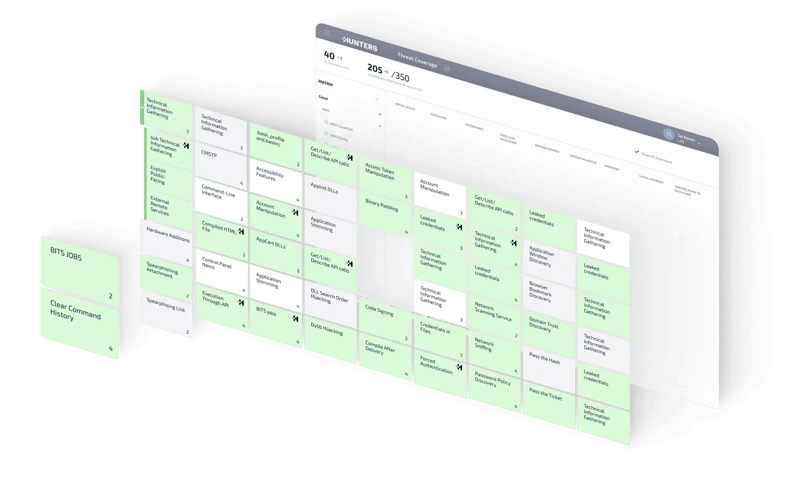
Cut investigation time
Automatic triage, enrichment and investigation reduce the noise and surface real, prioritized incidents so your team can clearly understand threats, their context and the necessary steps for remediation.
.png?width=800&height=533&name=investigation-new-(1).png)
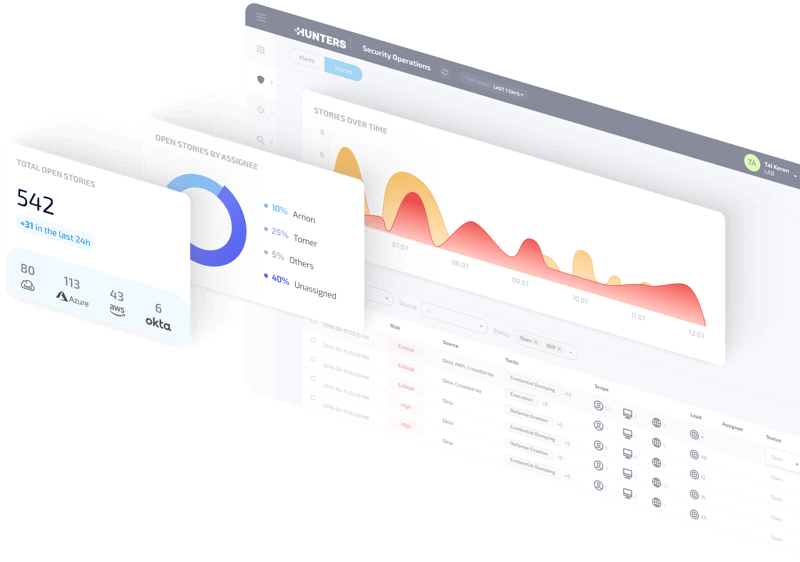
Respond with confidence
Clear Attack Stories that address the who, what, where and when of the incident empower fast attack understanding, expediting time to containment and MTTR.
.jpg?width=1200&height=800&name=RSA%20for%20website%20(1).jpg)