Move Beyond SIEM with Hunters and Snowflake
by Yael Macias, Head of Corporate & Customer Marketing
Mar 31, 2021Hunters recently hosted a webinar featuring Omer Singer, Head of Cyber Security Strategy at Snowflake. While we had an engaging discussion on the evolution of security operations, security as a data game, and detection and response workflows, there was one takeaway that stood out from the session: today’s SOCs are moving beyond legacy Security and Information Event Management (SIEM) solutions. They are doing so by adopting a security data lake with Extended Detection and Response (XDR) to streamline their security programs while achieving the automation and scale needed to detect and respond to threats when security becomes a big data challenge.
Deconstructing the SIEM
Security and Information Event Management (SIEM) solutions have traditionally been the center of the security operation. Ingesting firewall and endpoint logs from on-premises and other sources, it serves as the unifying platform for security telemetry, and the go-to place for security analysts to conduct investigations on incidents and alerts. However, as valuable as they have been, security teams increasingly report that SIEMs have become “costly, complex and resource-consuming” ( ESG’s survey research “The Impact of XDR in the Modern SOC ”).
If we break down the key use cases for the SIEM, we could tackle them from two key angles:
- Data aggregation and storage: collecting, normalizing and storing all event logs, also serving for auditing and compliance;
- Threat detection and response, based on manual rule configuration and alerting prompted by those rules or deviations from standard behavior.
But security practitioners are calling for a change: with siloed security and organizational data, overload of manual, time-consuming security analysis, and cost prohibitive license models, security operations are only becoming more difficult.
SOC Requirements Are Evolving
In a world where organizations generate petabytes of siloed data, it becomes crucial to move past rule-based threat detection and on to advanced analytics, while using cost-effective and scalable cloud storage to retain security data.
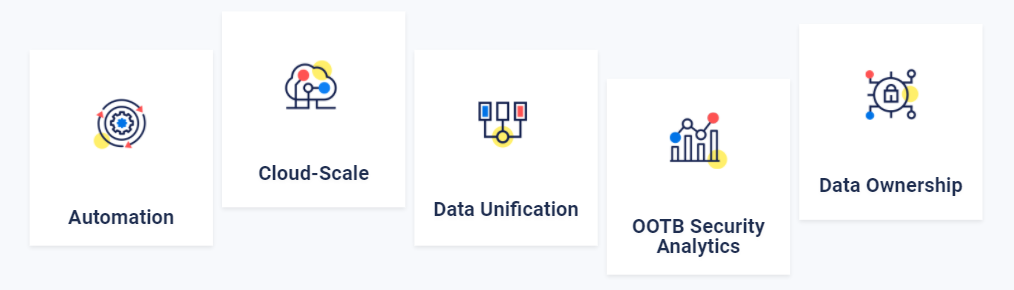
These are some of the key requirements of the modern SOC:
- Automation across the entire lifecycle of the security operation; from the data ingestion all the way to the detection of threats, enrichment of signals and response.
- Cloud-Scale which can support the exponential growth in security data volumes and complexity.
- Data Unification: it is no longer enough to have the data from the different sensors living in silos and using the SIEM for the more traditional sources – all data needs to be unified in order to enable cross-surface detection and response.
- Out-of-the-Box Security Analytics which give value off-the-shelf from day one. These should be complemented with the ability of security teams to write their own analytics for their specific use cases.
- Data Ownership, so teams can have full access to it, even when they switch security vendors. Owning the security data means they can query raw data as needed, and retain it for as long as necessary in a cost-effective manner.
Key Requirements of the Modern SOC
Security Data Lake and XDR
Security data lakes can support analytics at scale and at a fraction of the cost of dedicated SIEM solutions, preparing the organization for the petabyte-scale security challenges already arising. Adding XDR capabilities on top of it enables the consolidation of all security sources, regardless of who the security vendors are, and attaining out-of-the-box, intelligent analytics that deliver insights that the SOC can act upon.
Moving Beyond SIEM
Hunters’ native integration with Snowflake brings sophisticated threat detection to a customer’s data platform, empowering customers to utilize a single, scalable source of truth coupled with a state-of-the-art, open XDR solution. With virtually unlimited and cost-effective scalability, Snowflake is the ideal platform for centralized logging. The benefits of this approach, and the ease of getting started, are enabling security teams to move beyond the SIEM.
To learn more about replacing your SIEM using Hunters & Snowflake, watch the webinar hosted by Omer Singer, Head of Cyber Security Strategy at Snowflake. Schedule a custom demo to see the solution in action.
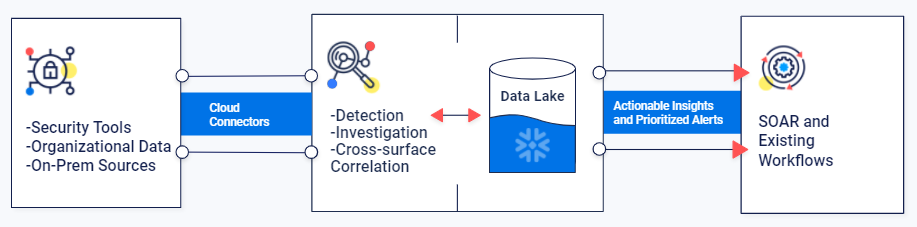
Hunters’ Integration with Snowflake’s Data Lake




