The Microsoft Threat Intelligence Center (MSTIC) recently released a blog post about a new supply chain campaign launched by the Russian nation-state actor Nobelium, the same actor behind the SolarWinds 2020 campaign. Microsoft observed this Nobelium supply chain campaign in May 2021 and since then, they have notified more than 140 resellers and technology service providers that have been targeted by Nobelium, of which probably 14 of them have already been compromised. These attacks have been a part of larger waves of attacks, targeting more than 600 Microsoft customers that have been attacked 22,868 times by Nobelium from July to the end of October 2021.
Nobelium's approach to this campaign was similar to the way they usually act, targeting and leveraging resellers and tech providers that have direct access to their customers' cloud IT systems. The APT group used simple attack techniques to steal the victims’ credentials - techniques such as password spraying, brute force, and phishing.
In this blog post, we present relevant information on the Nobelium attack and suggest detection methods and threat hunting flows that will help mitigate the attack.
Attack Overview
The Nobelium group likely has not used sophisticated TTPs or vulnerabilities, but rather this time their attack chain was based on social engineering to steal credentials and gain access to highly privileged users on the cloud service providers (CSP) and managed service providers (MSP) to ultimately compromise their downstream customers.
Let’s take a look at an example of an attack presented by the MSTIC:
An attack chain example
As the image illustrates, the APT group targeted IT providers, MSP, and CSP, leveraging legitimate business processes and procedures to get to their end target.
According to Microsoft, "the example demonstrates the breadth of techniques that the actor leverages to exploit and abuse trust relationships to accomplish their objective."
The attacks were mainly focused on the Azure platform, so the following proposed detections and threat hunting queries are focused on this cloud environment.
Hunters' Proposed Detection Methods
The different detection methods focus on advanced TTPs that the APT group employed in various manners. It’s important to mention that there are remediation tips (available on Microsoft's blog post) that we suggest taking into consideration before advancing to these advanced detection methods.
The following detection methods were implemented in the Hunters’ platform and probably would have detected the Nobelium attack, allowing further investigations:
1. Azure RunCommand - Detects the execution of a PowerShell script using Azure Run Command. The Run Command feature uses the Azure virtual machine agent to run PowerShell scripts within an Azure Windows VM. This feature was abused by Nobelium trying to shift access from cloud to on-premises.
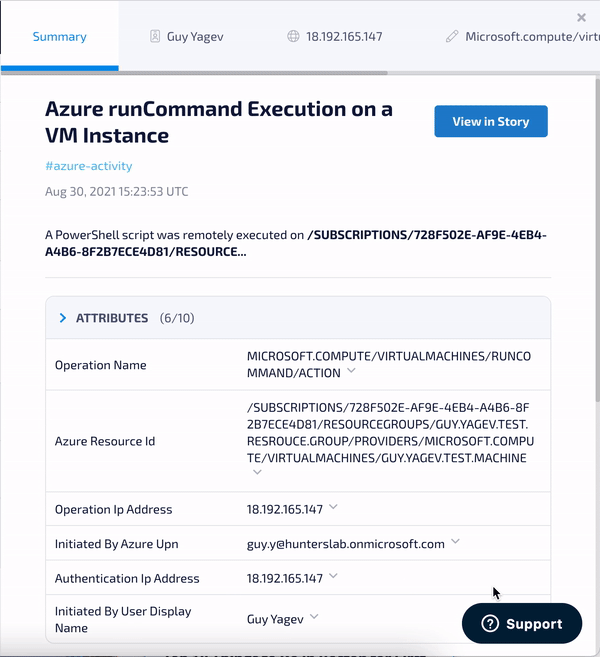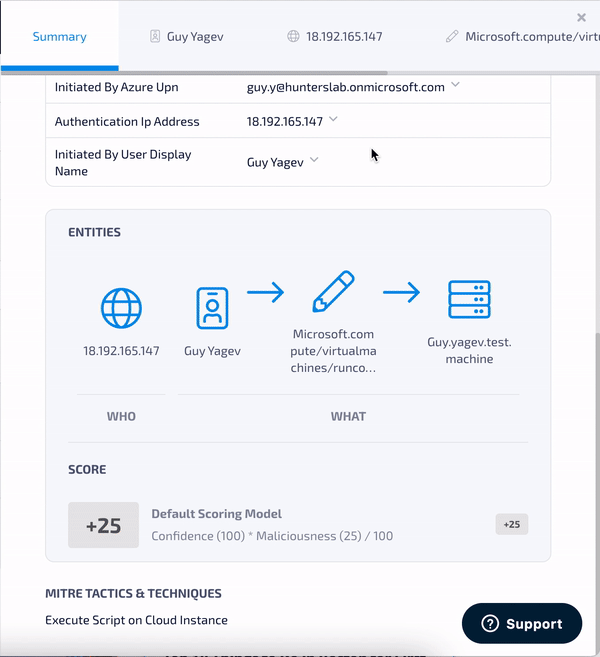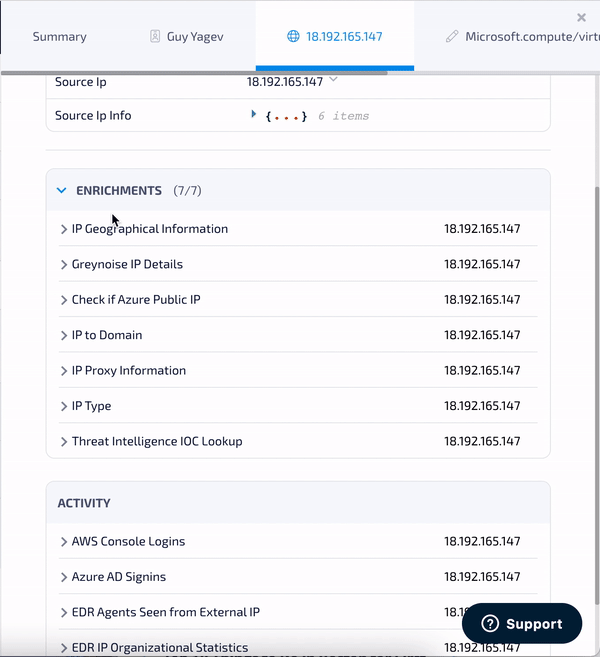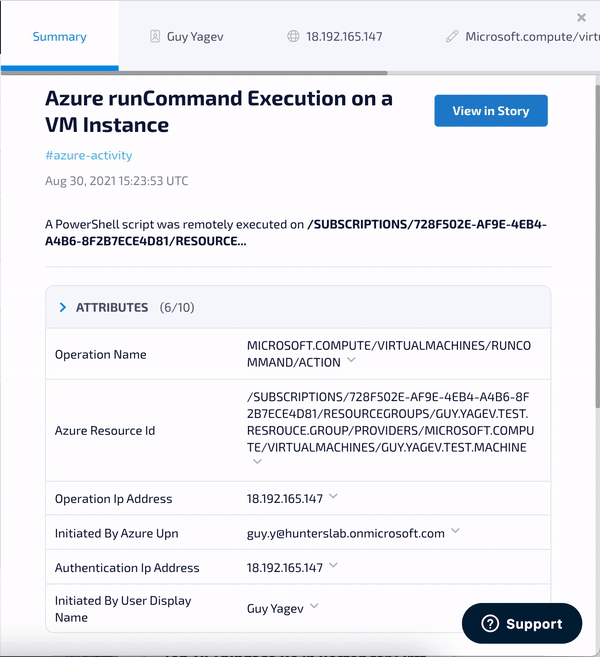
2. New OAuth Application Consent - Detects the grant of consent by a user to a new Azure application. Sophisticated threat actors are known to phish users with such malicious OAuth applications. Granting consent to these apps may allow them to read emails and access files on the user’s behalf.
.gif?width=504&name=ezgif.com-gif-maker%20(1).gif)
As can be seen in the GIFs above, we extract several attributes including IP address, user, and more, to be able to perform further investigations that will reveal to us if the threat signal is malicious or not.
In addition, with Hunters XDR, there are many Azure TTPs that are being covered as can be seen in the picture below.
[Learn more about how Hunters' open XDR leverages the MITRE ATT&CK framework to close threat detection gaps on this webinar.]
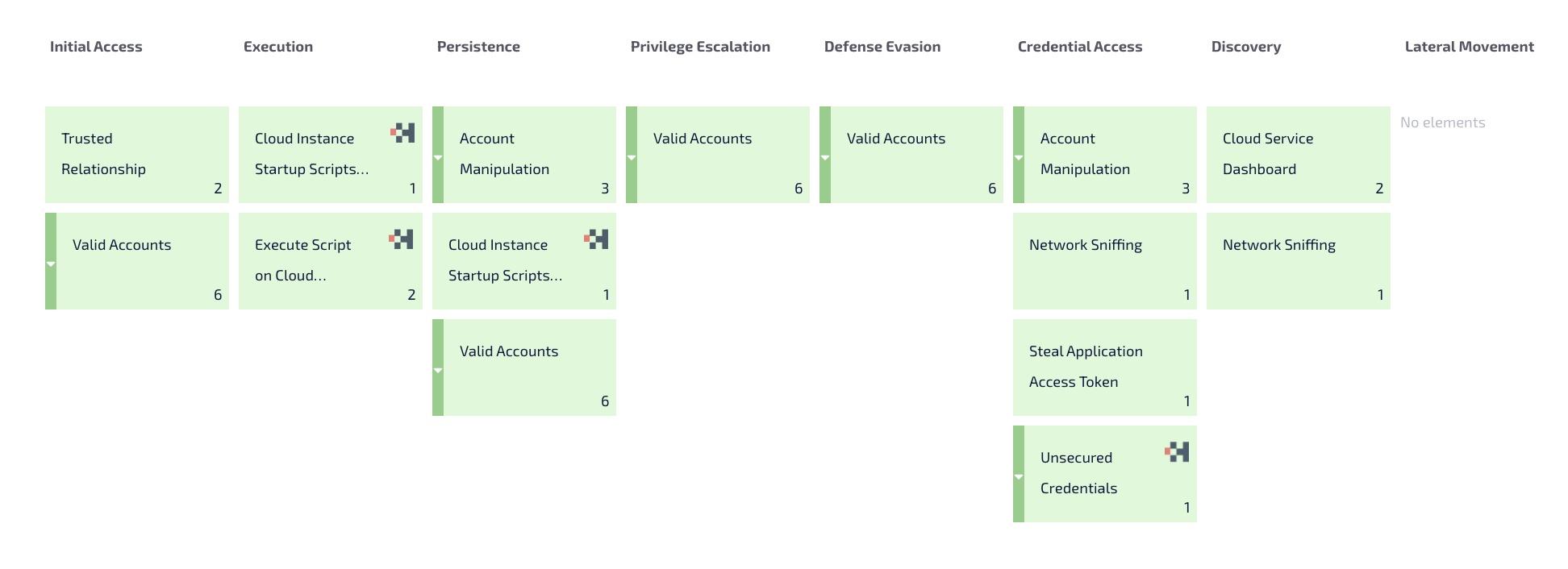
Hunters’ covered Azure TTPs
Threat Hunting Queries
In addition to the detection methods, we recommend using the queries below to hunt for suspicious activity in the environment. These threat hunting methodologies and more are conducted by our threat hunting team - Team Axon.
- User agents - The attackers were observed leveraging scripted tools for enumeration of the Azure AD which leads to authentications to Azure with user agents associated with scripts. (Note: these user agents can be modified by attackers for blending in the environment). Query logic:
- Group by user agent
- Filter out UAs with known key-words - for example ('%mozilla%','%dalvik%','%outlook%','%iphone%',’%ipad’)
- Count how many times this UA was observed
- Count from how many distinct IPs this UA was observed
- Look for UA observed from a low amount of IPs and not many times
- Logons from anomalous countries - Some of the attacks originated from TOR and proxy nodes located in countries that are probably anomalous in the wild.
- Group by country code
- Count distinct identities login from a country
- Look for country codes with a low amount of distinct user logons
- Reveal users logging in without MFA - Reveal hygiene gaps that can be exploited by an external attacker once the user’s password is compromised
- Query for enforcedGrantControls field
- Look for logons without MFA policy applied
Summary
Nobelium has been an active and frightening actor for two years now, targeting any potential victims that might be an opening for supply chain attacks, targets that manage their customers' environment.
We recommend taking prompt action to ensure the organization hasn't been compromised by this specific attack, as well as making sure that the detection methods and remediation tips are in place to avoid exposure to future supply chain attacks.
Hunters’ platform offers these detection methods built-in, with superb coverage that allows security teams to attain visibility into the attack surface as well as auto-investigations that surface high-fidelity signals should an attack take place.
Read our latest blog about “Minimizing the Risk of Supply Chain Attacks” here.




