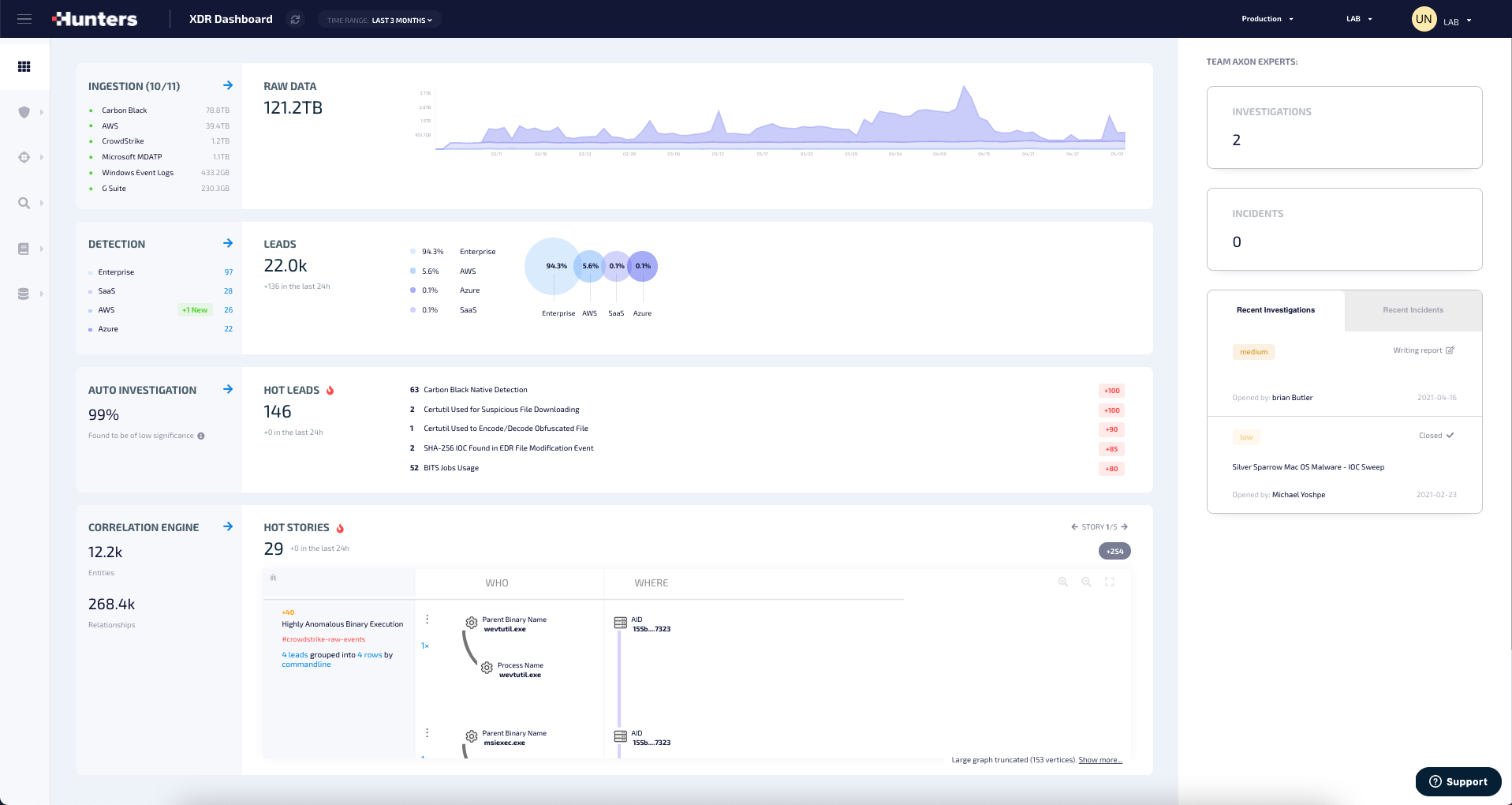
In the past few years, significant progress has been made in threat detection programs with the advancement and adoption of security tools like endpoint/EDR, network/NDR, identity/IAM, email, and cloud security tools. But despite the increased expectation from the new tooling, it hasn’t translated to an increased impact from security operations. While organizations now have sources of data indicating a breach, it is often not accessible, or complete, nor is it easily deciphered.
A few trends are causing security to become increasingly complex, hindering the effectiveness of teams tasked to protect organizations. At the core are the attackers with greater skills, tools and opportunities to exploit, forcing security teams to have a greater collective level of expertise to keep pace. The shift to the cloud, accelerated by the pandemic, requires new knowledge for securing cloud workloads. And the growing number of point security solutions, all firing their own alerts, require constant context switches to manage. Analysts need a security decision support system that augments their ability to identify, investigate and comprehend the nature of the attack activity, and clearly understand the appropriate response measures. Let’s look at how Open XDR helps achieve this.
It starts with data.
There is no doubt that data is a critical element to the success of security, but the criticality of data is not being served in today’s security models. We need to address the data dependency in a more complete way, improving its coverage and management:
- Visibility: We need access to all data. Threat actor sophistication doesn’t allow for compromise of how much or which data feeds we accept. Attackers are adept at hiding in our environments and data visibility across all sources is necessary.
- Usability: We need to intelligently process data. With expansive cloud and traditional environments, our organizations generate massive and varied amounts of data. Our systems need to be able to process this data into digestible forms to enable our detection engines to quickly and effectively investigate threat activity.
- Availability: Threat actors are savvy and persistent and remain dormant for weeks or months to quietly operate in our networks. Traces exist and long-term availability of data is a necessity for rapid investigation of attack activity, otherwise known as ‘hot storage’ of data.
Any form of compromise to these data elements, whether from single-vendor stacks limiting efficacy from data scope or forced data limits from escalating data charges, compromises all downstream security operations activity. The massive investment in tooling and people is undermined by models that fail to prioritize complete approaches to data.
An Open XDR framework is built with a holistic approach to data:
- Ingests all available security telemetry - from on-premises sources to the cloud
- Normalizes and unifies all the data into a single, digestible schema to facilitate analysis
- Retains the data over time ensuring sufficient coverage for incident investigation and forensics, and accelerates subsequent response measures.
Missing attack context means incomplete response
It is only when we have all the data available from across the attack surface, and cross-correlate all activities, that we can effectively expose malicious attack activity. But the purpose needs to shift from more detection and creation of alerts to building a picture of the attack. Existing detection and response programs put heavy emphasis on detection, but can lack an ability to offload activity from analysts and empower them with the knowledge to foster productive investigations.
Extended detection and response is more than a collection of broader data sources, but is a resulting evolution of the analyst’s ability to triage, investigate and understand the impact of the attack. The analyst’s clarity of the incident is what drives effective response: knowing the root cause, affected users and assets, and the timeline of events is a critical link for effective containment. Put another way, Mean Time To Respond (MTTR) can be a false indicator of what we are truly striving for, as we don’t just want to respond faster, we want to do it in an accurate and appropriate way. When we focus on better understanding the attack impact, the appropriate response measures are clear. And for that, the analyst needs visibility and clarity to all the aspects of an incident.
Often when we hear about breaches we are surprised to find out that the indicators and even the alerts existed, but that these were dismissed or overlooked. This is not the fault of the team: it is the result of the systematic failure to spot real incidents. Attackers leverage the plethora of alerts and erase their traces to blend in without being detected, making it challenging for analysts to uncover actual malicious activity. Only systems that can holistically look at all telemetry, and link together low-fidelity, seemingly unrelated indicators, can solve the issue of incidents being overlooked.
This is where the power of Open XDR comes into play. Open XDR drives accelerated and confident response through automated investigations and dynamic cross-correlation of signals.
Hunters' open XDR provides critical capabilities to augment an analyst’s ability to address sophisticated attacks. These include:
- Packaged deep security expertise: Ready-to-use adaptive detections built to identify unknown threats uncover a broader range of relevant signals.
- Threat-current Analytics: A continuous stream of threat analytics with real-time updates reduce the burden of detection engineering that analysts currently face.
- Machine Learning: Beyond expanding human capacity, machine learning facilitates automatic investigations and the cross-correlation and analysis of all signals, including elevating low-fidelity (appearing as benign) signals that are frequently hidden in typical detection capabilities.
- Dynamic Scoring: Applies sophisticated alert curation and prioritization to avoid skipped alerts based on security expertise and organizational context while also supporting customer parameters.
- Attack Stories: Curated and correlated signals and alerts are packaged into a contextual view of an incident for accelerated analyst understanding of the attack and its impact.
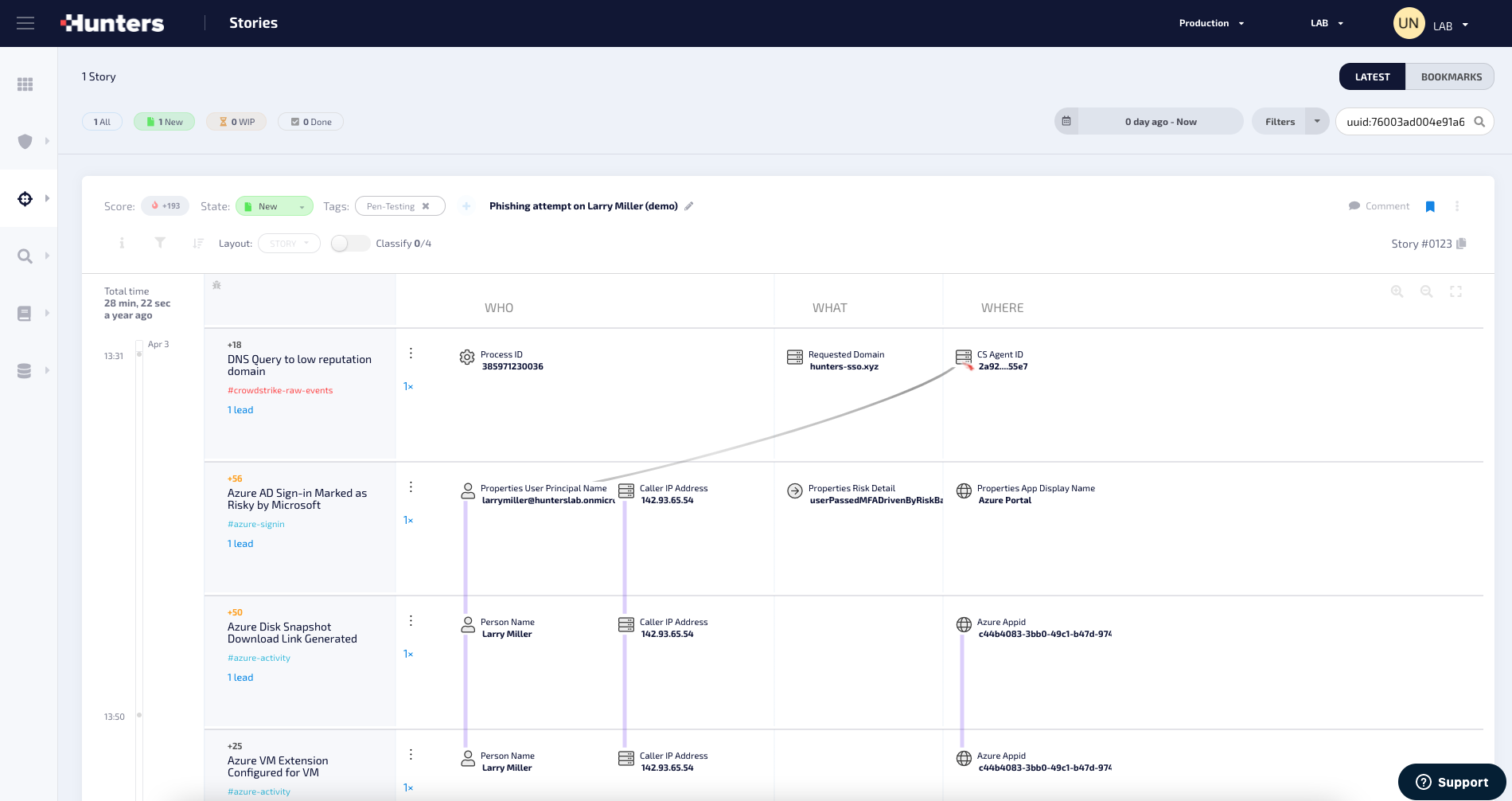
Timely, Specific Outcomes for Security Operations
At a time when CISO priorities include simplification and reduction of tooling to alleviate budgetary and performance drain, Hunters' open XDR provides the mechanism to tackle underlying gaps and challenges in security operations. The ability to finally digest and process vast amounts of data will not just increase performance but also facilitate improved results with positive outcomes:
- Leverage existing data within budget to optimize threat investigations
- Remove unnecessary and exhaustive rule-management workforce drain, which is typically limited to known threats
- Alleviate talent gaps with auto-investigations generating real attack pictures that accelerate analyst understanding of the impact and therefore confidence in knowing the appropriate response measures.
When a platform can effectively accelerate analysts’ ability to clearly understand incidents and appropriately act upon them, it fills a major gap in today's security operations workflows. Hunters XDR, with a complete approach to data and automated analytics, puts investigative power back in the analyst's hands.
Explore how this security operations transformation is delivered -
-png.png)





