GigaOm recently released their Autonomous SOC Radar, a report written by Andrew Green that highlights the key autonomous SOC vendors and equips IT decision-makers with the information needed to select the best fit for their business and use case requirements.
As defined in the report “autonomous security operations center (SOC) solutions reallocate security analysts’ processing power from conducting repetitive analysis and response tasks to only investigating incidents of significant interest and importance. Using correlation engines, calibrated alarms, workflow-based automation, integrations with internal and external intelligence feeds, and AI/ML-based operations, autonomous SOC solutions present analysts consolidated views of threats and act as a central management service for gathering information and resolving incidents.”
In the report it’s made clear though, that the SOC should not and will not be fully autonomous: existing tooling should help security analysts with volume and empower them to scale in a non-linear way, leveraging automation, AI and built-in workflows, but should not replace them in any way.
All solutions included in this radar report meet the following table stakes-capabilities:
- multiple ingest streams
- tunable alarms
- third-party tool orchestration
- workflow automation
- flexible storage
- dashboards and visualization
Hunters is recognized as a Leader and Outperformer and can be found in the Innovation/Platform Play quadrant, as it has comprehensive capabilities across the board and its automation and orchestration engines are natively built into the solution.
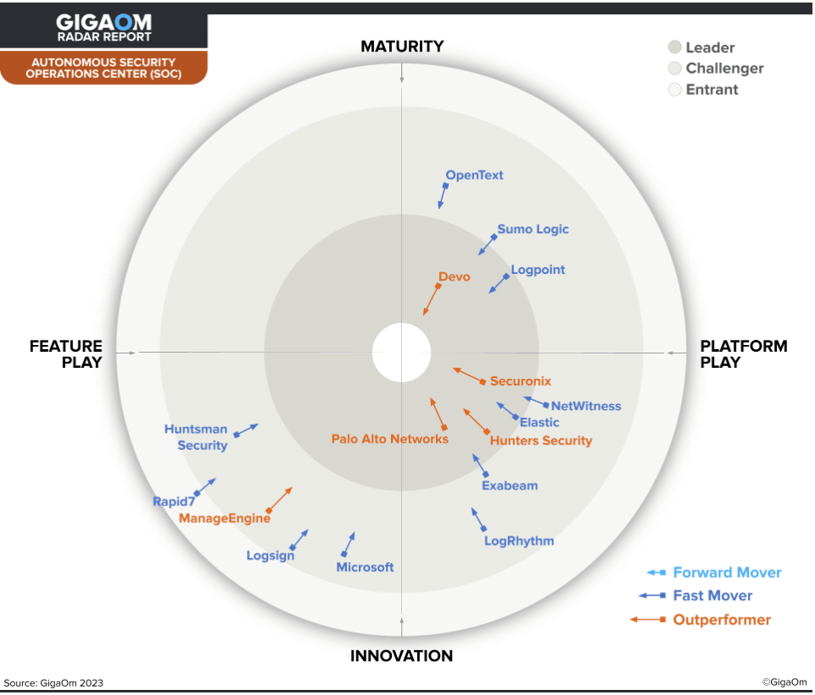
According to the report, Hunters is "a compelling SIEM replacement solution that scores well on the key criteria of behavioral analytics and contextual risk-based scoring and retrospective analysis and threats categorization.” Hunters is also listed as one of the report’s emerging technologies, scoring ‘exceptional’ on its focus and execution around security data lakes and content creation using Generative AI & LLMs.
Read the full report to access recommendations that will help your organization understand the key requirements to attaining autonomous capabilities for your SOC.




